Missing Access Control in uniswapV3SwapCallback Function
Notice: This page is a freshly imported case study from an original repository. While the original content had a similar format, some sections may not have been fully completed. Please help fill in any empty sections or any missing information you can find. If you are new here, please read General Tutorial on Wikis or Anatomy of a Case Study for help getting started.
Notice: This page contains sources which are not attributed to any text. The unattributed sources follow the initial description. Please assist by visiting each source, reviewing the content, and placing that reference next to any text it can be used to support. Feel free to add any information that you come across which isn't present already. Sources which don't contain any relevant information can be removed. Broken links can be replaced with versions from the Internet Archive. See General Tutorial on Wikis, Anatomy of a Case Study, and/or Citing Your Sources Guide for additional information. Thanks for your help!
A recent exploit on the Base chain targeted a smart contract at address 0x8d2e, resulting in a $40,000 loss in USDC due to improper access control on the uniswapV3SwapCallback function. This function is a core part of Uniswap V3’s architecture and must be secured to ensure only trusted Uniswap pools can invoke it. In this case, the attacker exploited weak validation logic—likely simulating a valid callback—to trick the contract into releasing funds. Although some protections may have been in place, they were ineffective, reflecting a broader trend of inadequate safeguards around Uniswap V3 integrations. The exploit was confirmed by multiple security firms and reported by SuplabsYi. There’s currently no evidence of recovery or formal investigation, and the contract’s owner remains unknown.[1][2][3][4][5][6][7][8]
About Uniswap
Uniswap is a decentralized exchange (DEX) protocol built on Ethereum and other EVM-compatible blockchains that enables users to trade cryptocurrencies directly from their wallets without the need for intermediaries. It uses a unique automated market maker (AMM) model, where liquidity providers deposit token pairs into liquidity pools, and traders interact with those pools to execute swaps. Instead of relying on a traditional order book, Uniswap determines pricing through a mathematical formula that balances the ratio of tokens in the pool. This allows for continuous, permissionless trading and deep liquidity across a wide range of token pairs.
Uniswap V3, the third major version of the protocol, introduced several advanced features, including concentrated liquidity and multiple fee tiers. Concentrated liquidity allows liquidity providers to allocate their capital within specific price ranges, increasing capital efficiency and improving returns. Additionally, the protocol is modular, with a core set of smart contracts that handle pool logic and a periphery set that manages user-friendly routing and interface functions. Uniswap is widely used across DeFi for swaps, arbitrage, liquidity provision, and integration into other DeFi platforms, making it one of the most influential protocols in the ecosystem.
About uniswapV3SwapCallback
The uniswapV3SwapCallback is a critical function in the Uniswap V3 protocol that facilitates token swaps by ensuring the correct token amounts are transferred during a swap operation. Specifically, it's a callback function that must be implemented by any contract that initiates a swap via the Uniswap V3 pool’s swap function. When a swap is executed, the Uniswap V3 pool contract calls uniswapV3SwapCallback on the calling contract, providing it with the exact amounts of tokens that must be paid back to the pool in order to complete the swap.
The callback function receives three parameters: int256 amount0Delta, int256 amount1Delta, and bytes calldata data. The amount0Delta and amount1Delta indicate the net token amounts that must be returned to the pool — a positive value means that the token must be sent to the pool, while a negative value indicates an amount received from the pool. The data parameter is passed through from the original swap call and can be used to decode custom data required for processing the swap. Importantly, this callback mechanism allows for powerful features like flash swaps, composable DeFi operations, and on-the-fly pricing logic, making Uniswap V3 highly flexible and programmable. Implementing this callback correctly is essential for any smart contract interacting directly with Uniswap V3 pools.
The Reality
Unfortunately, any smart contract with insecure access restrictions can be vulnerable to be exploited.
What Happened
A smart contract on Base chain was exploited for $40,000 in USDC due to weak access control on the uniswapV3SwapCallback function, allowing an attacker to simulate a legitimate callback and drain funds.
| Date | Event | Description |
|---|---|---|
| August 20th, 2025 10:42:55 AM MDT | Attack Transaction On Base | The attack transaction is processed and incorporated into the history of the Base blockchain. |
| August 20th, 2025 10:46:00 AM MDT | Weilin Analysis | Weilin (@hklst4r) posts about the attack transaction with a high level description. |
| August 20th, 2025 12:16:00 PM MDT | SupLabsYi Analysis | Yi (@SupLabsYi) posts a more detailed analysis of the exploit transaction with further details. |
| August 20th, 2025 8:26:00 PM MDT | TenArmor Posts Tweet | TenArmor posts a tweet which features details of the attack, along with another attack which occurred recently. |
Technical Details
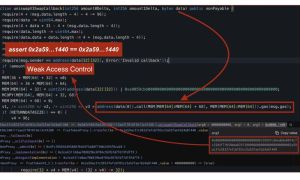
The exploit of contract 0x8d2e on Base chain highlights a recurring security flaw in Uniswap V3 integrations—improper or missing access control on the uniswapV3SwapCallback function. This callback is a required part of the Uniswap V3 protocol; it gets called by the pool after a swap() function is invoked, expecting the calling contract to transfer the owed token amounts. However, because this function can be externally triggered, failing to restrict who can call it opens the door to direct manipulation. In this case, the attacker likely invoked uniswapV3SwapCallback with carefully crafted calldata, simulating a legitimate swap to trick the victim contract into transferring funds.
Historically, developers attempted to secure uniswapV3SwapCallback by hardcoding known Uniswap V3 pool addresses and checking that only these pools could invoke the callback. But that approach is fragile: pools can be forked, misconfigured, or spoofed, and hardcoding values doesn't scale or adapt well to ecosystem changes. Worse, it gives a false sense of security. In the 0x8d2e case, the contract included some form of validation, but the logic was either flawed or insufficiently enforced, allowing the attacker to simulate a valid call and drain around $40,000.
The broader issue here is a design pattern that fails to account for the trust boundaries in DeFi. While Uniswap V3 gives developers flexibility, it assumes implementers will enforce strict controls in their uniswapV3SwapCallback logic. When they don't—whether due to oversight or incorrect assumptions—the results are catastrophic. In this instance, what may have seemed like a reasonable design backfired entirely. The attacker didn’t break the rules—they simply played by the ones left exposed. Going forward, developers must validate the msg.sender as a known, trusted pool created by the Uniswap V3 factory and rigorously verify swap parameters to ensure they match expectations. Anything less is an open invitation for exploits.
Total Amount Lost
Losses were analyzed as $40k by SuplabsYi. This matches with the blockchain transaction indicating that $40k worth of USDC were transfered.
The total amount lost has been estimated at $40,000 USD.
Immediate Reactions
It is unclear who runs this smart contract. The incident was reported on by at least 3 separate security firms.
Ultimate Outcome
There does not appear to be any formal investigation underway.
Total Amount Recovered
There is no evidence that any recovery is possible.
There do not appear to have been any funds recovered in this case.
Ongoing Developments
This situation could develop further if the perpetrator is identified.
Individual Prevention Policies
No specific policies for individual prevention have yet been identified in this case.
For the full list of how to protect your funds as an individual, check our Prevention Policies for Individuals guide.
Platform Prevention Policies
Policies for platforms to take to prevent this situation have not yet been selected in this case.
For the full list of how to protect your funds as a financial service, check our Prevention Policies for Platforms guide.
Regulatory Prevention Policies
No specific regulatory policies have yet been identified in this case.
For the full list of regulatory policies that can prevent loss, check our Prevention Policies for Regulators guide.
References
- ↑ TenArmor - "Another two hacks: The victim contract 0x8d2e was exploited due to missing access control in the uniswapV3SwapCallback function. Someone approved tokens to the Multicall3 contract, resulting in the tokens being drained." - Twitter/X (Accessed Aug 21, 2025)
- ↑ Hklst4r - "Another uniswap V3 unprotected callback hack. base chain" - Twitter/X (Accessed Aug 21, 2025)
- ↑ SuplabsYi - "Looks like another uniswapV3SwapCallback-related hack, with a total loss of $40,000. The root cause? The access control mechanism for uniswapV3SwapCallback is pretty weak, letting malicious actors manipulate data and bypass the controls." - Twitter/X (Accessed Aug 21, 2025)
- ↑ IUniswapV3SwapCallback — Uniswap Docs (Accessed Aug 21, 2025)
- ↑ IUniswapV3PoolActions - Uniswap Docs (Accessed Aug 21, 2025)
- ↑ SwapRouter Interface - Uniswap Docs (Accessed Aug 21, 2025)
- ↑ Introduction to the Uniswap Protocol - Uniswap Docs (Accessed Aug 21, 2025)
- ↑ Uniswap V3 Core Whitepaper (Accessed Aug 21, 2025)